One of the best password managers we’ve seen, 1Password comes from their Extended Access Management (XAM) suite.
By combining 1Password Enterprise Password Manager (EPM) and 1Password SaaS Manager, organizations can discover and manage corporate credentials with Zero Trust Access Governance.
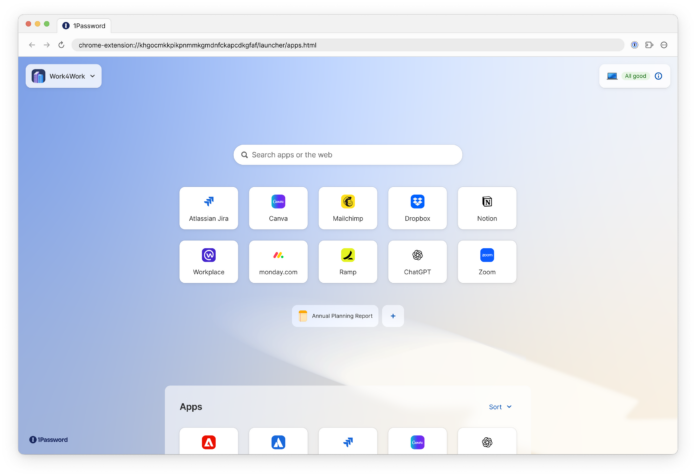
Unified Access simplifies credential tracking across spreadsheets, documents, vaults, and employees, consolidating credential management for every application and platform your business relies on in one place.
Unified Access Now Available
Business growth often leads to the use of new applications and platforms throughout the organization.
Parts of the organization invest in SaaS tools without notifying IT teams, resulting in “shadow IT” (unmanaged applications used by employees without IT skills) and “SaaS sprawl” (widespread use of software-as-a-service applications by teams within an organization without IT skills, resulting in unnecessary expenses and redundant tools).
The sudden appearance of new identifiers can quickly overwhelm IT administrators due to the large volume of identifiers that must be tracked and managed. Add to that the comings and goings of employees, and it can become a serious security problem.
In fact, more than a third (38%) of employees admitted to accessing a previous employer’s accounts after leaving the company. If handled improperly, disgruntled former employees could exploit their qualifications to cause untold damage.
Unified Access allows administrators to discover and manage credentials by searching the organization’s EPM vault for stored credentials and then managing them centrally through Unified Access.
Access to credentials can also be controlled by revoking employee access when they change roles or leave the organization. Unified access capabilities also help administrators meet governance requirements such as SOC 2, ISO 27001, and HIPAA by creating logs for each access and login event.
The app launcher also simplifies access for employees because each single sign-on (SSO) and non-SSO application used by an employee is centralized and access is granted with a single click, without the employee having to know or enter the required username or password.
This eliminates the need to search for credentials for every application an employee needs, potentially increasing efficiency and productivity.
The public preview of 1Password Unified Access will be available starting January 13 and is open to existing 1Password EPM Business customers in US-hosted environments with at least 100 users.
To further explore the power of unified access and the potential benefits it can bring to organizations struggling to manage credentials, I spoke with Jason Meller, VP of Product Architecture at 1Password:
- What are the key benefits that a CISO could communicate to senior management to justify the investment in unified access?
Most organizations already have identity tools, but access is no longer entirely within them. SSO and IAM are necessary, but they don’t cover a large and growing area of real-world access: shared team accounts, administrator credentials, seamless access, and the long list of SaaS applications that never integrate with SSO. Risks accumulate in this gap.
Unified Access is designed for this reality. Govern federated and non-federated access from a single location, rather than forcing security teams to consolidate multiple tools and processes. By consolidating credential management, SaaS discovery, and application access into a single system, organizations reduce exposure to unmanaged credentials, simplify access workflows, and improve audit readiness without increasing operational overhead.
For the company, this means lower risks and greater control without slowing down teams. Employees have a single, consistent way to access all the applications they need, and security teams gain visibility and accountability across SSO and non-SSO environments. It is access that reflects how modern organizations really work: distributed, rapidly evolving and no longer limited to a single identity system.
- How can organizations leveraging remote/hybrid work and BYOD policies benefit from unified access capabilities?
Remote and hybrid work has not only changed the workplace, but also the way access works. Employees log into work apps from personal devices outside of a managed network, often using credentials that never go through SSO.
Unified Access moves governance to the access layer itself. IT and security teams can manage, revoke, and audit access to SSO and non-SSO applications, regardless of device ownership or location. Shared and sensitive credentials remain centrally protected and access can be updated or revoked instantly as roles change or people leave the company.
This avoids friction losses for employees. They have a reliable way to access everything they need, anywhere, without having to manage or share passwords. For security teams, it provides consistent, auditable access control that can support distributed and high-BYOD environments without trying to fit everything into a traditional perimeter model.
- What information does Unified Access provide about device-level security and shadow IT, and how does Unified Access provide continuous authentication in a perimeterless environment?
In a world without perimeters, security cannot depend on trusted networks or fully managed devices. Unified Access focuses on securing the access itself rather than assuming the environment is trustworthy.
This gives security teams a clear view of what applications and credentials are actually being used, including shared and sensitive accounts that are typically outside of SSO. Monitoring SaaS credential usage and access uncovers hidden paths and unmanaged applications that traditional IAM tools often miss.
Each access event is assignable. Role changes, credential usage, and access revocation are logged and can be audited.
Access may be removed immediately if conditions change. The result is continuous visibility and access control, even when employees work from anywhere, on any device, and without defined perimeters.
- Will Unified Access availability expand to smaller businesses once the public preview is complete, and if so, what types of support will be provided to businesses that don’t have a large IT team to handle a more complex setup?
Yes, after public preview, Unified Access will be generally available to all organizations of all sizes. For organizations with smaller IT teams that can’t justify SSO for every application or manage complex identity infrastructure, Unified Access can be a solid solution.
By protecting access to SSO and non-SSO applications, it centralizes access and management of shared and sensitive credentials. This allows small teams to manage access consistently, even when SSO coverage is not practical or complete.